Sponsored by Tenable
Sponsored by Panorays
The CISO’s Guide to Choosing an Automated Security Questionnaire Platform
Sponsored by Panorays
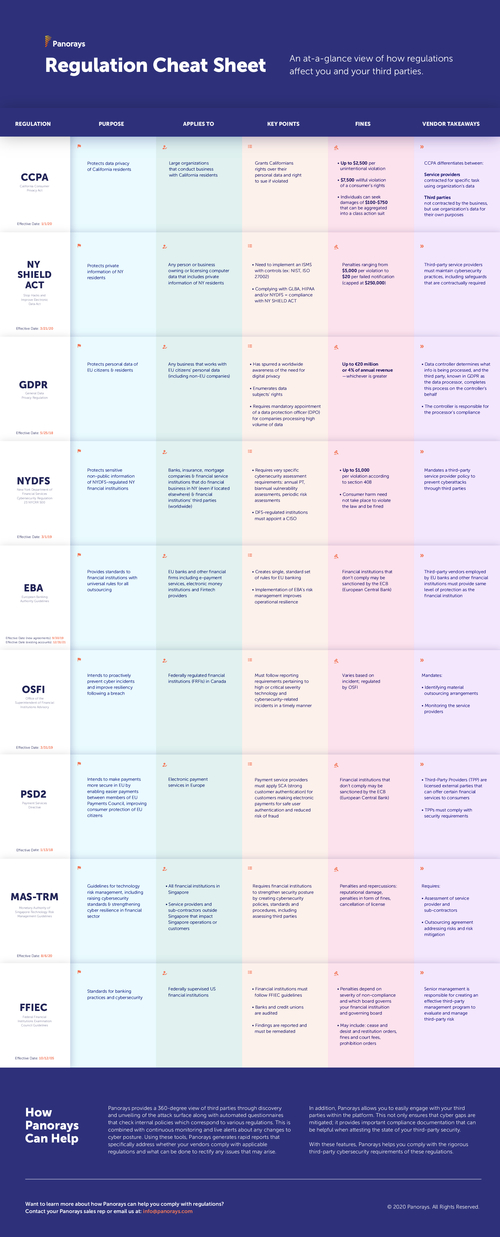
Regulation Cheat Sheet
Sponsored by Panorays
The CISO's Guide to Third-Party Security Management
Sponsored by Cisco
SASE For Dummies
Sponsored by Red Hat
Boost Hybrid Cloud Security
Sponsored by Palo Alto
Cloud Security Blind Spots: Detecting and Fixing Cloud Misconfigurations
Sponsored by Skurio
The Essential Guide to Digital Risk Protection
Sponsored by Skurio
How to Reduce Digital Risk in a Post-COVID World
Sponsored by Barracuda
The Evolution of Email Security
Sponsored by CyberGRX
CyberGRX Exchange Insights
Sponsored by Ordr
5 Ways to Improve Asset Inventory and Management Using Ordr
Sponsored by Gigamon
TLS Versions: North-South and East-West Web Traffic Analysis
Sponsored by Omada