Sponsored by Vercara
Sponsored by Colt
Fighting The New DDoS Threat
Sponsored by Colt
Automated Distributed Denial of Service Attack Mitigation
Sponsored by ManageEngine
How to Defend Against DDoS, Ransomware and Cryptojacking
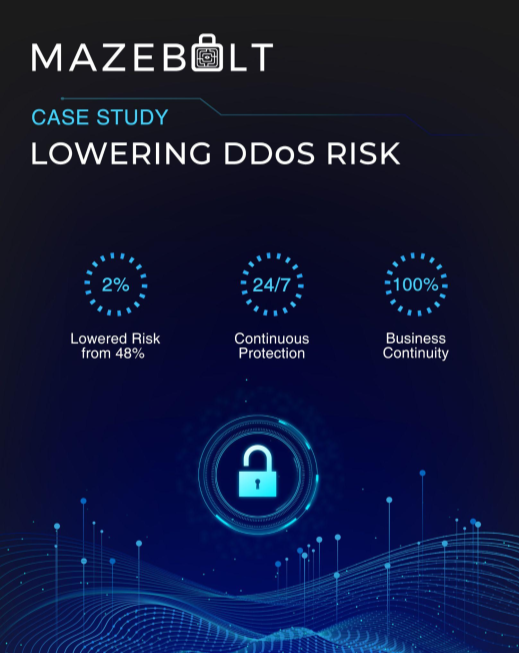
Sponsored by Mazebolt
Case Study | Lowering DDoS Risk
Sponsored by Mazebolt
A Simple Guide to DDoS Mitigation
Sponsored by Akamai
DDoS Defense in a Hybrid Cloud World
Sponsored by Sophos
Quantifying the Business Impact of Threat Protection
Sponsored by Sophos
How to Ensure You're Not Part of the Next Botnet
Sponsored by Neustar
UltraDDoS Protect Success Stories
Sponsored by Flashpoint
Compromised Credentials Monitoring Brief
Sponsored by Flashpoint
Pricing Analysis of Goods in Cybercrime Communities
Sponsored by Neustar
2019 Year in Review Cyber Threats & Trends
Sponsored by Splunk
The SOAR Buyer's Guide
Sponsored by eSentire