Critical Infrastructure Security , Cybercrime as-a-service , Cyberwarfare / Nation-State Attacks
US Energy Utilities Targeted by FlowCloud Malware
Proofpoint Analysts Find Connections Between New Trojan and Other Attacks
In late 2019, several U.S. energy providers were targeted by a spear-phishing campaign attempting to spread a recently discovered remote access Trojan called FlowCloud, according to research published by security firm Proofpoint.
See Also: Russian Programs Threatening Critical Infrastructure
The campaign took place between July and November 2019, using lures that mimicked an industry association in order to entice the targeted victims to click on malicious attachments that would attempt to install the FlowCloud malware, according to Proofpoint. The report did not name any of the energy utilities targeted in this campaign.
If the malware is successfully executed, FlowCloud enables the attackers to gain a foothold in targeted networks, take complete control of infected devices, gather intelligence and exfiltrate data, according to the report.
"Fundamentally, FlowCloud is a remote access Trojan, and while there are plugins and modules aimed at remote access Trojan objectives, we have not identified any additional functionality that would suggest destructive intent," Sherrod DeGrippo, senior director of threat research and detection at Proofpoint, tells Information Security Media Group.
"While the attacker intent is perhaps the most opaque and difficult thing to ascertain about a campaign, it appears that the goal of these campaigns was likely to establish an initial foothold in target systems and gather intelligence via the FlowCloud remote access Trojan's capabilities," DeGrippo says.
While it's not clear if any of the spear-phishing emails associated with this recent campaign were successful, the Proofpoint researcher did find connections between FlowCloud and another series of attacks from 2019 that targeted U.S. utilities using malware called LookBack (see: LookBack Malware Campaign Spreads to More US Utilities).
Proofpoint researchers also now believe that these two separate campaigns are the work of one hacking group that the analysts refer to as TA410, although little is known about this group's motivations.
Infection Tactics
The phishing campaign attempting to distribute the FlowCloud RAT came in two parts, according to the report. In July 2019, the attackers sent phishing emails that used portable executable attachments with the subject line: "PowerSafe energy educational courses (30-days trial)."
The second wave of phishing attacks, which started in November 2019, used messages that contained attached malicious Microsoft Word documents. These emails purported to come from the American Society of Civil Engineers and spoofed the organization's domain and logos to lure its victims, according to the Proofpoint report.
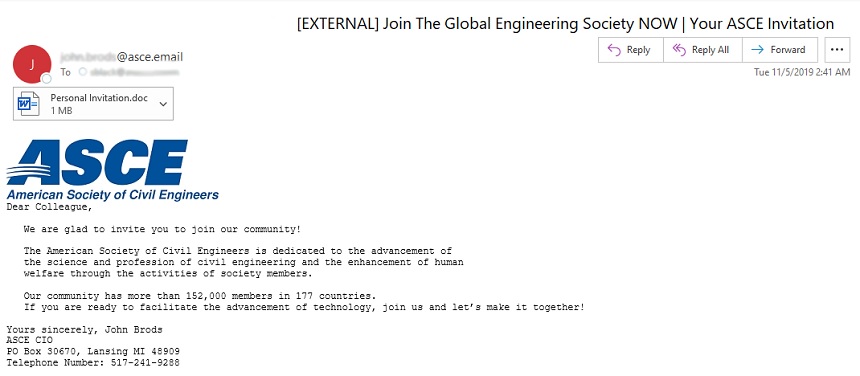
Both the Word and portable executable documents contained malicious macros. If these were enabled by the targeted victim, the FlowCloud malware would then be downloaded from a DropBox URL, according to the report.
Proofpoint researchers note that FlowCloud has been specifically designed to target Windows system and is equipped with a key logger in order to access data from installed applications as well as the keyboard, mouse, display, internal files and other services.
After the malware identifies the data it wants to steal, the information is encrypted using a modified AES algorithm and compressed using Zlib, a software library used for data compression. The data is then exfiltrated to a command-and-control server, according to the report.
When the Proofpoint researchers examined the emails that contained the FlowCloud malware, they found similarities between these messages and those used to deliver LookBack. This includes a similar use of macros and overlapping infrastructure.
In the case of LookBack, the attackers disguised their messages to make them appear to come from the Global Energy Certification - an organization that offers education certificates and training for those working in the energy industry.
TA410
In addition to identifying a single hacking group behind these campaigns, the Proofpoint researchers also noted similar techniques and tools used by TA410 and another hacking organization called TA429.
TA429 is also referred to as APT10 and has connections to China, according to security firm FireEye. And while the two groups use similar techniques and tools, the Proofpoint researchers suspect this might be an attempt by TA410 to disguise itself or create additional confusion through a false-flag operation.
"The crossover between TA410 and TA429 is not definitive," DeGrippo says. "Proofpoint analysts believe that intentional reuse of well-publicized TA429 - APT10 - techniques and infrastructure may be an attempt by threat actors to create a false flag to cloak the identity of the threat actor while they targeted a critical and geo-politically sensitive sector of energy providers in the U.S."
Attacks Targeting Utilities
Over the past several years, security researchers have noted an uptick in malicious campaigns targeting electrical and power utilities in the U.S. and elsewhere.
In March, for example, the European Network of Transmission System Operators, which represents over 40 electricity transmission operators throughout the continent, revealed that hackers penetrated its IT network (see: Hackers Target European Power Association)
DeGrippo notes that these types of attacks must be tracked.
"Over the past year, there has been a slight increase in the volume of attacks aimed at those in the utilities sector," DeGrippo tells ISMG. "This does not indicate that the threat is less serious or that those in the sector should not continue to focus on defensive strategies. Threats using attachments in emails is steady while URL-based threats have slightly increased year over year. Credential phishing is a larger threat by volume to utilities versus malware threats when observed in email delivery."
Managing Editor Scott Ferguson contributed to this report.