Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development , Ransomware
Shadow Brokers Promises Exploit of the Month Club
Equation Group Hackers Try to Blame Microsoft, NSA for Ransomware Worm Debacle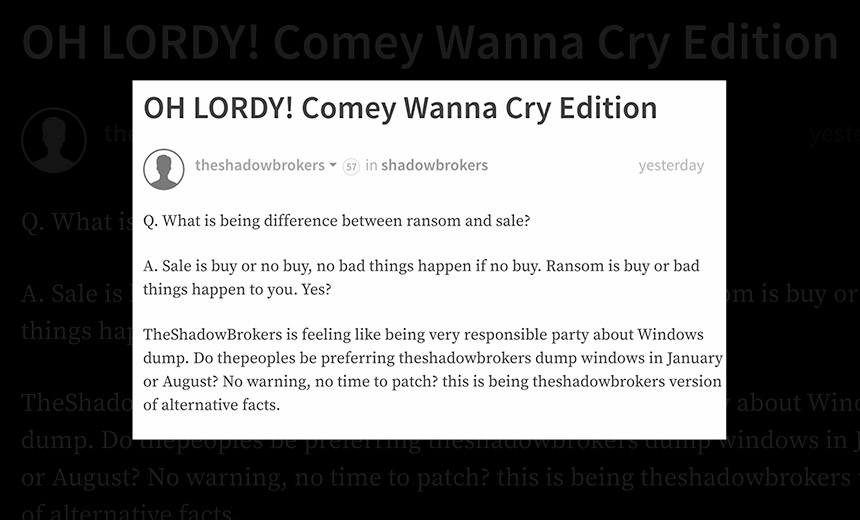
The group whose leak of U.S. spying tools aided the WannaCry outbreak says it will soon sell fresh software exploits and intelligence. It also hinted that the blame for the WannaCry outbreak should go to Microsoft and the U.S. government.
See Also: OnDemand | Fighting Cybercrime: Insights and Strategies for Finding Bad Guys in Your Environment
The comments from the Shadow Brokers arrived just five days after WannaCry crippled businesses and organizations across the world, infecting at least 200,000 endpoints with file-encrypting malware (see WannaCry Ransomware Outbreak Spreads Worldwide).
Little is known about the Shadow Brokers, which first set up online shop in August 2016. Some speculate it may be a disgruntled U.S. government employee or a foreign intelligence agency (see Mystery Surrounds Breach of NSA-Like Spying Toolset).
In a long, difficult-to-read blog post Tuesday, the Shadow Brokers implies the new exploits and tools come from the Equation Group. That's the nickname for what's believed to be the NSA's Tailored Access Operations, the former name for its network infiltration unit.
The Shadow Brokers says it will offer the data as part of a monthly subscription service, which it will unveil next month. The data may include exploits for mobile devices, routers, web browsers, Windows 10 and other tools, it says.
The group additionally claims to possess data on providers of SWIFT - the messaging system used for international wire transfers - and central banks. It also claimed to have "compromised network data from Russian, Chinese, Iranian or North Korean nukes and missile programs."
Damaging Dumps
Careful analysis of the Shadow Brokers' previous data dumps has left little doubt that the group somehow gained access to troves of sensitive U.S. government information.
In August 2016, the group released a surprising sampling of spying tools and exploits that it claimed originated with the Equation Group. It was a teaser for a larger batch of tools that the Shadow Brokers attempted - but failed - to auction. Subsequently, the group in early January promised that it would withdraw from the public eye.
But on April 14, it reappeared, releasing a new, large dump of data. Included was a potent software exploit, nicknamed EternalBlue in documents labeled as being "top secret." The exploit targeted a vulnerability in the Windows server message block (SMB) protocol, which is used for file sharing. All versions of Windows except the latest one were vulnerable.
That leak eventually fuelled the largest ransomware attack on record. Whoever developed WannaCry then used the exploit to distribute its ransomware, while also adding a self-replicating capability that had a devastating impact.
Although Microsoft patched the SMB flaw in its newer operating systems in March, and then issued an emergency patch of older systems in May, tens of thousands of computers worldwide had not been updated, thus allowing the ransomware to spread. Although experts advise speedy patching, organizations often delay until quality checks are completed to ensure other applications aren't hampered by the software changes.
Computer security companies and researchers have found similarities between an earlier version of WannaCry and malware used by the Lazarus Group, which many suspect is affiliated with North Korea (see Is WannaCry the First Nation-State Ransomware?).
Not Interested in Grandma's Pension
The Shadow Brokers' post included its first commentary on WannaCry. The group appears to argue that it responsibly disclosed EternalBlue, giving Microsoft plenty of time to patch.
The group says that it posted screenshots in January of a "2013 Windows Ops Disk" belonging to the Equation Group. It claims that was enough to tip off Microsoft to the vulnerability and for it to begin preparing a software patch.
In fact, the screenshots were alarming, so much so that the U.S. Computer Emergency Response Team on Jan. 16 issued a warning of a potential SMB security vulnerability, advising administrators to disable it and block certain ports. Had that advice been widely followed, WannaCry wouldn't have had nearly the impact that it ultimately had.
Vulnerability Reporting Timelines
Ethical security researchers give software companies time to patch before publicly disclosing details of flaws. The time period varies, but vendors usually get a least a month, in theory allowing them to close the hole before hackers can independently discover and begin exploiting it.
Asked how it learned about EternalBlue, Microsoft declined to comment to Information Security Media Group, except to say that it might withhold identifying any bug hunters who request to remain anonymous.
In an irregular move, Microsoft skipped its scheduled monthly patch-release day in February before resuming on March 14, at which point the company quietly fixed many vulnerabilities that the Shadow Brokers then released one month later, in April.

The Shadow Brokers appears to claim that its own timing was deliberate and that its only intention for leaking the attack tools was to demonstrate that the Equation Group was hacked. It also suggests North Korea was behind the WannaCry ransomware outbreak.
"TheShadowBrokers is not being interested in stealing grandmothers' retirement money," the group writes in its awkward English. "This is always being about theshadowbrokers vs theequationgroup."
The group goes on to skewer Microsoft President and Chief Legal Officer Brad Smith, who on Sunday issued pointed criticism of the U.S. spy agencies for stockpiling vulnerabilities. He contended that such practices put civilians in danger if cybercriminals come into possession of the information (see Post-WannaCry, Microsoft Slams Spy Agency Exploit-Hoarding).
Finally, the Shadow Brokers claims that Microsoft and the Equation Group may have closer ties than they have publicly acknowledged. But that argument is hard to follow due to the Shadow Brokers' poor English, which some observers believe may be intentional.






















