Application Security , Incident & Breach Response , Next-Generation Technologies & Secure Development
Report: APTs Adopting New Phishing Methods to Drop Payload
Hackers Using Rich Text Format Template Injection to Bypass Anti-Malware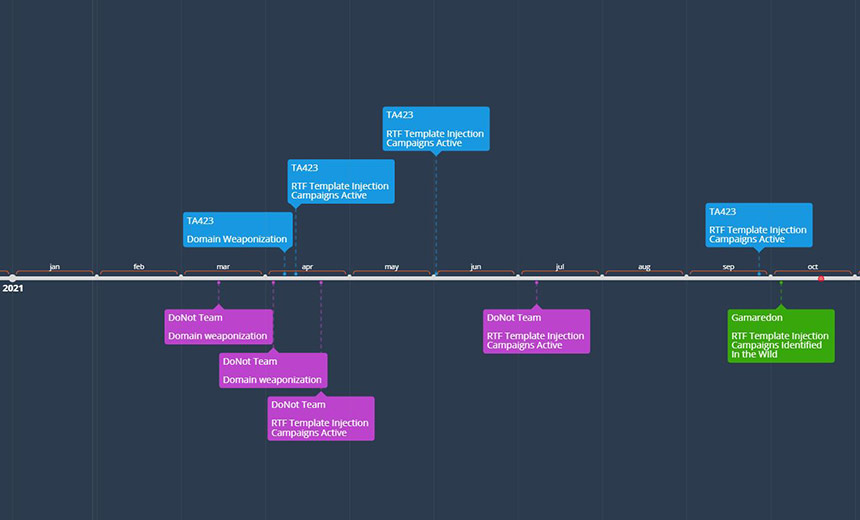
Multiple APT groups from Russia, China, and India are adopting a new phishing attack technique, using Rich Text Format, or RTF, template injection, which makes their attacks harder to detect and stop, researchers warn.
See Also: Panel Discussion | The 2021 Global State of Security
RTF template injection is a technique in which an RTF file containing decoy content can be altered to allow for the retrieval of content hosted at an external URL upon opening an RTF file. The template is compatible with Microsoft Office, which makes it easier for a user to open or edit these documents, giving attackers an opportunity to attack any system.
Proofpoint researchers first observed the increasing adoption of RTF template injection from February 2021 through April 2021, but the researchers say this technique was first seen as early as January 2021.
The Proofpoint threat researchers assess with moderate confidence that this novel technique could be adopted by other financially motivated cybercriminals.
What’s New?
"This technique, referred to as RTF template injection, leverages the legitimate RTF template functionality. It subverts the plain text document formatting properties of an RTF file and allows the retrieval of a URL resource instead of a file resource via an RTF’s template control word capability," says Michael Raggi, senior threat research engineer at Proofpoint.
The process enables an adversary to replace a file destination with a URL from which a remote payload may be retrieved. In the next stage, the retrieved payload can be loaded into an application or steal Windows credentials. The researchers say that since the payload is not in the document but in a shared URL, an antivirus will scan the RTF file and mark it safe, even though the URL is malicious.
Using Lures
The researchers say that a malicious payload can be retrieved using .doc.rtf file, which is an extension that specifies an RTF file will be opened with Microsoft Word.
"When an RTF Remote Template Injection file is opened using Microsoft Word, the application will retrieve the resource from the specified URL before proceeding to display the lure content of the file. This technique is successful despite the inserted URL not being a valid document template file," Raggi says.
Researchers demonstrated a process in which the RTF file was weaponized to retrieve the documentation page for RTF version from a URL at the time the file is opened.
"The technique is also valid in the .rtf file extension format, however a message is displayed when opened in Word which indicates that the content of the specified URL is being downloaded and in some instances an error message is displayed in which the application specifies that an invalid document template was utilized prior to then displaying the lure content within the file," Raggi says.
The weaponization part of the RTF file is made possible by creating or altering an existing RTF file’s document property bytes using a hex editor, which is a computer program that allows for manipulation of the fundamental binary data.
"This technique does not require the use of a word processor application for the injection of the RTF remote template URL into the file," the researchers say.
“Nation-state groups tend to innovate first with new attack vector variations and this would seem to be the case in this example," says Jason Steer, principal security strategist at threat intelligence company Recorded Future. He says the attack vectors have a short shelf life, which makes it difficult for the infosec community to learn about them.
Steer also says other problems exists: Not enough vendors can work and play together well and the security industry is terrible at sharing intelligence, which he says is the best way to enable security tools to be more effective at identifying these risks as they emerge.
Timeline of RTF Template Adoption
The researchers identified two distinct APT groups associated with the state interests of India and China that adopted RTF template injection earlier this year. Russian use of the technique has also been observed.
Proofpoint researchers attribute these template injection RTF files to the APT group DoNot Team, which is suspected of being aligned with Indian-state interests, identified through July 8, 2021. The researchers also identified a Chinese-related APT actor likely using RTF files to target entities with ties to Malaysian deep water energy exploration as recently as Sept. 29, 2021 (see: Chinese APT Group Reportedly Develops Custom Backdoor).
"Following this initial adoption period, the APT actor Gamaredon, which has been linked to the Russian Federal Security Service (FSB) was later observed utilizing RTF template injection files in campaigns that leveraged Ukrainian governmental file lures on Oct. 5, 2021," the researchers say.
In June 2021, Check Point researchers uncovered an ongoing campaign by a Chinese advanced persistent threat group that had spent the last three years testing and refining a custom backdoor in its arsenal to conduct espionage campaigns targeting governments in Southeast Asia.
During the investigation, researchers found that the campaign starts with a spear-phishing email containing malicious DOCX documents, which is sent to different employees of a government entity in Southeast Asia.
The document delivers an RTF file that is weaponized with what Check Point calls the RoyalRoad exploit builder, which takes advantage of users who have failed to patch older vulnerabilities in Microsoft Word’s Equation Editor.
Expect RTF Use to Continue
"We would expect to see this sophisticated attack appearing more widely in 2022 as the technique trickles down to cybercriminals and, as phishing will still be the main attack vector, the importance of regular and up-to-date anti-phishing awareness and simulation training becomes ever more important," says Alan Calder of GRC International Group, a provider of IT governance, risk management and compliance solutions.
"The moral of the story is that adversaries will continue to evolve or modify their tactics and that your anti-malware solution will ultimately fall short of providing confidence that at any given moment a user, asset or workload has not been compromised," says Tim Wade, technical director, CTO team at cybersecurity company Vectra AI.
"Managing this inevitable compromise with visibility, detection and response is the hallmark of modern enterprise security programs resilient to motivated adversaries, and their legacy peers that continue to struggle with the disruption of a successful attack," Wade says.
"Weaponized documents that require enabling downloads or other connections to external content aren't new. In this case, the methods used by attackers are novel because they can hide malicious URLs through the use of Rich Text Format's capabilities, either by embedding raw text or through the use of Unicode and other means," says Sean Nikkel, senior cyberthreat intel analyst at digital risk protection solutions provider Digital Shadows.
Nikkel says users should be wary of opening documents that require downloads of templates or other data from the internet, especially from unknown users. Organizations may want to restrict file types such as RTF, strip inbound emails of attachments, or use a sandbox to test them for malicious activity.














