Fraud Management & Cybercrime , Fraud Risk Management , Next-Generation Technologies & Secure Development
Ransomware Analysis: 'Shade' Surges; Other Trends Emerge
Researchers Explain Resurgence in Ransomware, Persistence of Exploit Kits
Attacks tied to Shade ransomware continue to surge as part of an overall resurgence in ransomware, security researchers warn.
See Also: The State of Organizations' Security Posture as of Q1 2018
Meanwhile, another strain of ransomware called Cyborg has been distributed via fake Windows Update emails that grab malicious executables from GitHub, researchers say. And while the use of exploit kits might be down - including for distributing malware - they're far from extinct.
Cybersecurity firm Group-IB says that in the first half of this year, Shade was the most prevalent strain of malware it saw, accounting for 53 percent of all malicious code spotted in the wild.
Shade was first distributed via malicious spam emails in October 2018, reported Juraj Janosik, a senior software engineer at cybersecurity firm ESET. Earlier this year, ESET charted a spike in malicious JavaScript attachments to emails that were designed to distribute Shade, especially against targets in Russia, he says.
Added Features: Cryptocurrency Mining, Click Fraud
Group-IB says that Shade - also known as Troldesh, XTBL, Trojan.Encoder.858 and Da Vinci - is easy to buy or rent and has continued to be upgraded. "The most recent Shade campaigns show that it now does not just encrypt files, but also can mine cryptocurrency and generate phony traffic on websites to increase revenue from ad fraud," Group-IB says in a blog post.
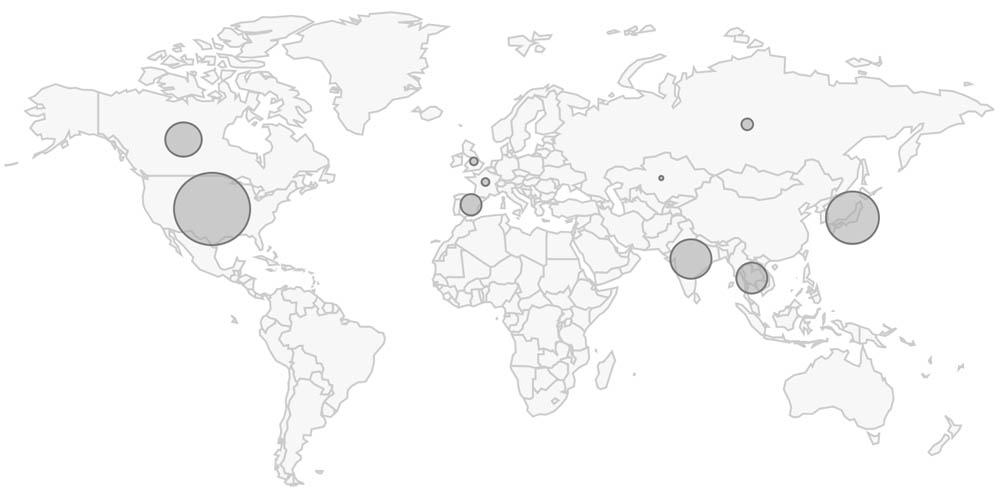
Shade has predominantly targeted Russian victims, but includes decryption instructions in both Russian and English. Even so, Brad Duncan, a security researcher at Palo Alto Networks' threat intelligence group Unit 42, reported in May that the top five most-targeted countries didn't include Russia or any former Soviet states, but rather the United States, Japan, India, Thailand and Canada, with Russia placing seventh.
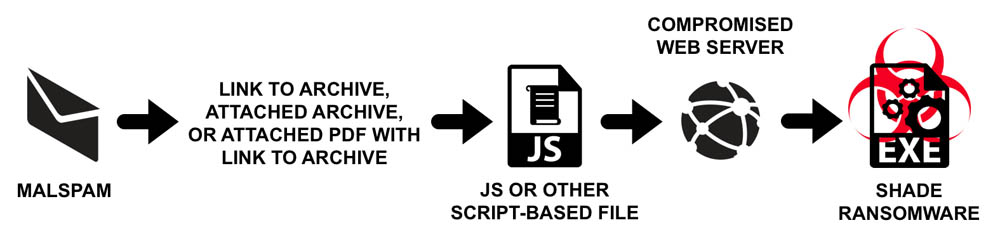
How can victims tell if their systems have been cryptolocked by Shade? "Since June 2016, file extensions for any encrypted files are .crypted000007," Duncan says.
Shade has been on the scene for some time, having first been spotted in 2014. The ransomware was on the long list of malware that was being installed by the infamous botnet called Andromeda - aka Gamarue or Wauchos - onto infected PCs, together with Carberp and Ursnif banking Trojans; Fareit and Kasident distributed denial-of-service attack malware; the Fynloski backdoor; as well as Cerber and Petya ransomware. At least that was the case until an international police operation, led by the FBI, disrupted Andromeda, leading to the arrest of a suspected ringleader in Belarus in December 2017 (see: Researchers: Andromeda Bust Collared Cybercrime Mastermind).
Trojan RTM and Pony Also Prevalent
Group-IB says the second most-seen strain of ransomware in the first half of this year was Trojan RTM, developed by a hacker group of the same name. It debuted in 2016 and originally used the Russian social networking service LiveJournal to handle command-and-control operations. Group-IB says the malware was originally designed to commit fraud via Russian financial services firms' "remote banking services," although more recently it has attempted to infect victims via drive-by attacks launched by trojanized sites with a financial services theme as well as via phishing attacks.
The third most prevalent type of malware in the same timeframe was the Pony downloader, which is designed to "steal victims' passwords from over 100 applications, including browsers, email clients, messengers, FTP and VPN clients," as well as to download and install additional malware onto infected endpoints, Group-IB says.
Targeting Trends
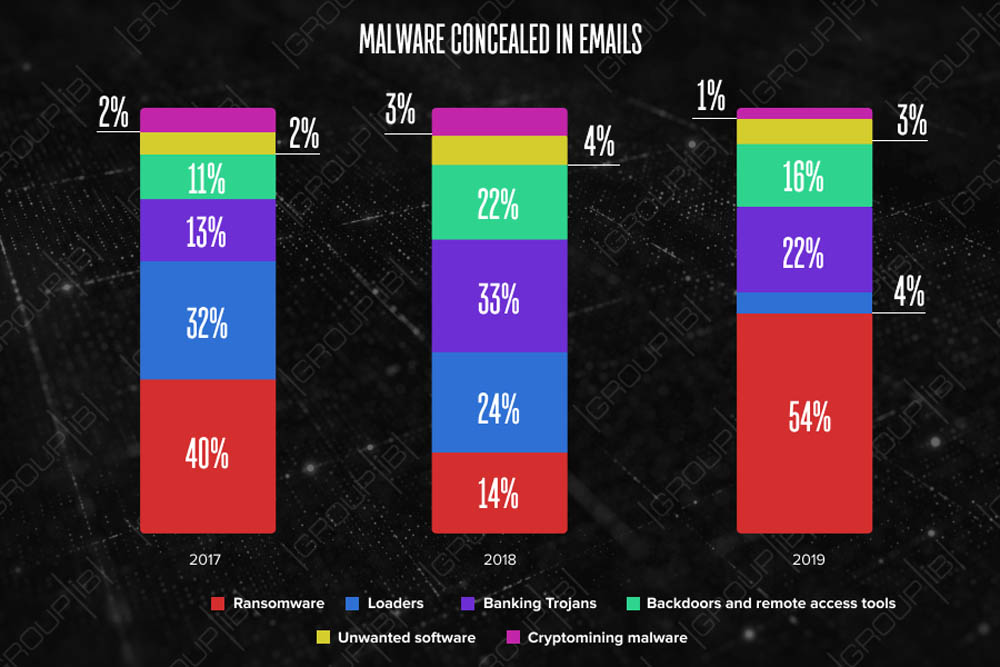
Based on attacks seen in the first six months of the year, Group-IB has identified several trends.
- Email attackers favor attachments. So far this year, Group-IB says 29 percent of email-borne malware was being delivered via links included in messages, compared to 71 percent arriving via email attachments.
- Archives are hot. Of those attachments, 80 percent were delivered in an archive format - .zip files, 32 percent of the time and .rar files, one-quarter of the time. "Threat actors included the passwords for accessing the contents in the subject of the email, the name of the archive or in their subsequent correspondence with the victim," Group-IB says.
- Finance and accounting are targeted most. Making messages look attractive - and authentic - continues to be key to their getting opened by victims, with accounting and finance groups continuing to be disproportionately targeted. Group-IB says the most popular subject lines for emails containing malicious attachments this year have been payment, scan, invoice, voice message and new order.
Geography-Based Perspectives
Group-IB's findings stand in contrast to some other security firms' analyses (see: Malware Most Foul: Emotet, Trickbot, Cryptocurrency Miners).
For example, CrowdStrike says that in the first half of this year, the most prevalent strains of malware seen in the wild - and being used in non-targeted attacks - were Emotet and Trickbot, followed by various strains of cryptocurrency mining malware, Gozi and Dridex.
But such findings aren't absolute. Rather, they reflect a security company's global view of attacks. Given that Group-IB was founded in Moscow and is now based in Singapore and sees many attacks based on what is targeting its customers, naturally the firm has its own view of the top threats in the wild, compared with Sunnyvale, California-based CrowdStrike or security firms in other geographies.
Ransomware Executable: 'bitcoingenerator.exe'
Ransomware writers continue to vary their bag of tricks. One recent attack seen in the wild, for example, used emails with the subject line "latest critical update" that directed recipients to execute an attachment that would purportedly facilitate Windows Update.
But instead, the attack was designed to download an executable - "bitcoingenerator.exe" - written in .NET and hosted at GitHub, says Diana Lopera, a security researcher at Trustwave SpiderLabs, in a blog post.
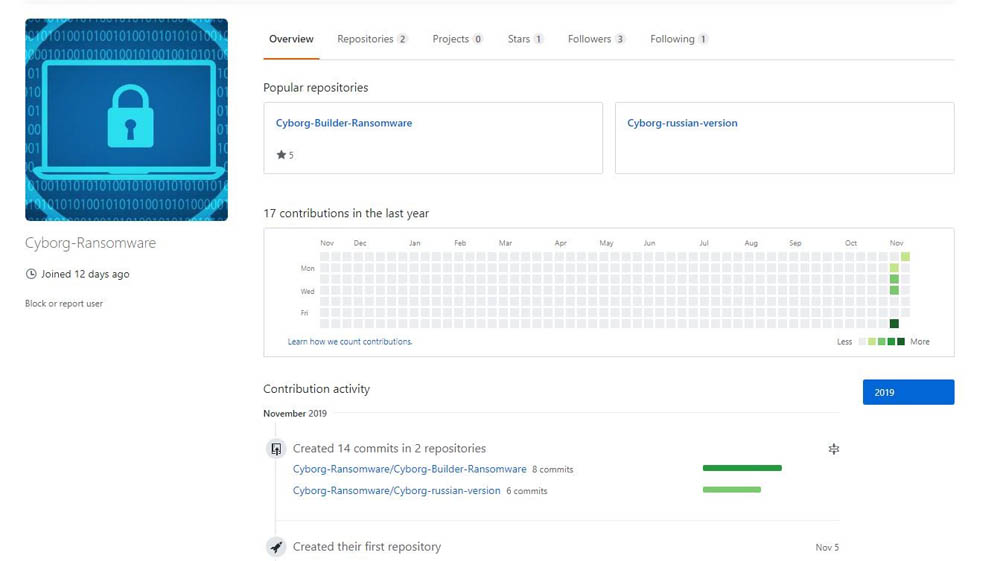
Lopera says that executable was a strain of ransomware called Cyborg. She notes that the "misterbtc2020" GitHub account hosting a ready-to-deploy version of the ransomware has been suspended, interrupting what had been an unsuccessful attack campaign, but that a Russian-language builder for the ransomware is still available via another GitHub account.
The choice of GitHub for hosting the malicious software was likely down to the code-sharing site's easy availability. "Most likely it was posted by a single cybercriminal or group of cybercriminals simply as a public, highly available location to distribute but also to help others interested in deploying ransomware or to collaborate with others," Trustwave SpiderLabs tells Information Security Media Group. "Ransomware has been widely used to successfully attack organizations and governments and having it and its builder hosted on the software development platform GitHub is significant. Anyone can grab a hold of it and create their own Cyborg ransomware executable."
So far it's not clear how many people may have been hit by attackers wielding Cyborg. "We don't have any idea how many people have downloaded the ransomware and the builder from GitHub but what we can say is that as of Wednesday, the YouTube video about the ransomware builder - pointing to the GitHub account Cyborg-Ransomware as the "download source" - already had 316 views," Trustwave SpiderLabs says. "That's 49 more views in approximately 24 hours after we made the screenshot of the said YouTube account for the blog. It's not viral but if known and misused by a person with the necessary technical skills, another wave of this spam campaign could spread."
Exploit Kits Keep on Ticking
Like ransomware, exploit kits have also been declared dead or dying, only to resurge - at least partially (see: Neutrino Exploit Kit: No Signs of Life). Historically, the success or failure of exploit kits was typically tied to the ready availability of widely installed software with easy-to-exploit flaws. Typical targets included Internet Explorer and various plug-ins, such as Adobe Reader, Java Runtime Environment and Adobe Flash Player.
SInce browser makers added auto-updating and Microsoft ditched IE in favor of the rewritten Edge - and plug-in makers also added auto-updating and started taking security more seriously - exploit kits have offered less bang for the buck.
Even so, Jerome Segura, a security researcher at Malwarebytes, reports this week that a number of exploit kits remain active, primarily targeting long-patched flaws in Internet Explorer (CVE-2018-8174) and Flash Player (CVE-2018-15982), among other vulnerabilities.
Nine of the top new or established exploits kits currently being seen in the wild, he says, are Spelevo, Fallout, Magnitude, RIG, GrandSoft, Underminer, KaiXin, Purplefox and Capesand.
Meanwhile, exploit kit operators have continued to refine their tactics. "Even though the weaponized vulnerabilities remain fairly old, we’ve observed a growing number of exploit kits go for fileless attacks instead of the more traditional method of dropping a payload on disk," Segura says. "This is an interesting trend that makes sample sharing more difficult and possibly increases infection rates by evading some security products."
Exploits kits are being used to distribute various types of malware. "In the past quarter, we’ve observed sustained malvertising activity and a diversity of malware payloads served," he says. "We can probably expect this trend to continue and perhaps even see new frameworks pop up. Even if it remains remote, we can’t discard the possibility of an exploit kit targeting one of the newer browsers."
This story has been updated with additional comments from Trustwave SpiderLabs.






















