Cybercrime , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime
Leak Exposes OilRig APT Group's Tools
Group, Apparently Backed By Iran, Was Broadening Its Targets, Analysts Say
A set of malicious tools, along with a list of potential targets and victims, belonging to an advanced persistent threat group dubbed OilRig has leaked online, exposing some of the organization's methods and goals, analysts say.
See Also: Global Ransomware Threat Report H1 2022
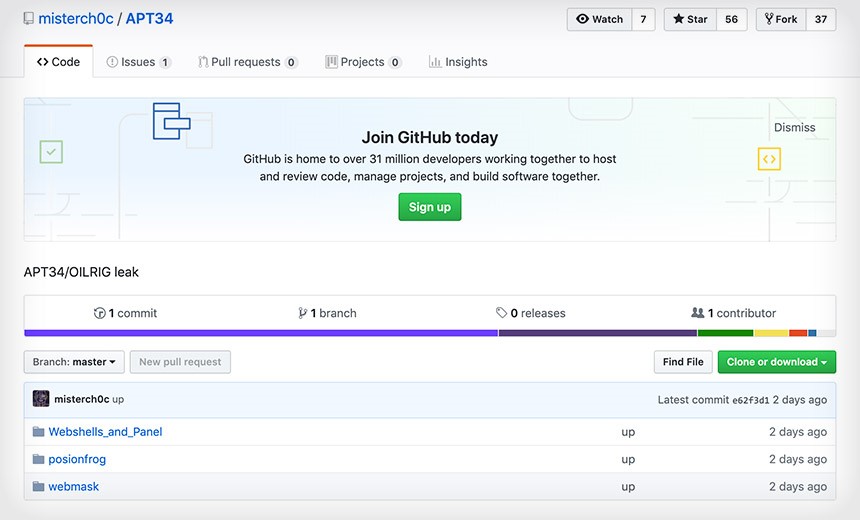
It's not clear how the OilRig material was exposed. But the malicious tools and the source code has been available since at least mid-March on Telegram and Github, according to security analysts, such Alphabet's Chronicle and others, who have verified the material. The list of victims and targets is only posted on Telegram, analysts say.
OilRig, which also goes by the name APT34 and HelixKitten, is apparently backed by Iran and has been active in the Middle East, according to a previous analysis by Palo Alto Network's Unit 42. The data that is now available, however, shows that the APT group has also had an interest in parts of Europe, Asia and Africa, as well as China.
Active since at least 2016, OilRig has targeted governmental agencies and businesses, including companies in the financial, energy, chemical and telecommunications sectors, as part of an ongoing and long-term espionage campaign. The APT group is primarily known for using DNS tunneling, a method that takes advantage of flaws in the DNS protocol to funnel malware and other malicious data through a target server, according to Unit 42.
The group is likely to change its strategy because some of its source code has been exposed online, says Brandon Levene, the head of applied intelligence at Chronicle, a cybersecurity firm that examined the leaked material.
"It's likely this group will alter their toolset in order to maintain operational status," Levene says. "There may be some copycat activity derived from the leaked tools, but it is unlikely to see widespread use."
Who Leaked OilRig Data?
It remains unclear who leaked the OilRig tools and data. A Twitter discussion about the disclosure offers some taunts against OilRig and its backers.
— 0xffff0800 (@0xffff0800) April 17, 2019
"We are exposing here the cyber tools (APT34/OILRIG) that the ruthless Iranian Ministry of Intelligence has been using against Iran's neighboring countries, including names of the cruel managers, and information about the activities and the goals of these cyber-attacks. We hope that other Iranian citizens will act for exposing this regime's real ugly face," according to one post that is attributed to a group that calls itself Lab Dookhtegan | Read My Lips, which says it helped post material on Telegram, according to security researchers.
At least three distinct OilRig tools appear on Github and Telegram:
- Glimpse, an updated version of BondUpdater - a PowerShell-based Trojan first discovered by FireEye;
- PoisonFrog, an older version of the BondUpdater Trojan;
- Hypershell, a version of what Unit 42 calls the TwoFace Webshell toolset, which enables the attackers to gain remote access to a network.
In addition, the Telegram site has a list of OilRig victims and targets, which includes organizations such as the Emirates Federal Competitiveness and Statistics Authority, the Emirates Prime Minister Office and the Oman Administrative Court, according to the Lab Dookhtegan page.
Hacking DNS
Over the last three years, OilRig has become gradually more sophisticated as the list of its targets and victims have grown, according to the Unit 42 analysis.
The APT group has started to take advantage of the some of the weaknesses found in DNS, according to Unit 42. DNS is an older protocol that acts as the "phone book" for the internet by taking domain names and translating them into a numeric code.
The Unit 42 analysis found that OilRig uses DNS tunneling to communicate between the victim and the group's command-and-control servers. This is also the method for delivering Trojans to the target systems.
"Regardless of the tool, all of the DNS tunneling protocols use DNS queries to resolve specially crafted subdomains to transmit data to the C2 and the answers to these queries to receive data from the C2," according to Unit 42.
Eyeing the Middle East
On Wednesday, Cisco Talos researchers described another unrelated attack, called Sea Turtle, that involves misuse of the DNS protocol. That attack involves stealing passwords and credentials as part of a sophisticated espionage campaign.
The Cisco Talos team did not name the nation-state that is backing Sea Turtle, but noted that the group is not associated with other groups, including OilRig, that have started to take advantage of DNS protocols for spying operations throughout the Middle East.